ArrayOS ASF 3.0.0.1 supports the function of inserting the client IP address into HTTP requests for the specified HTTP profile. After this function is enabled for an HTTP profile that is applied to a security service, client IP addresses that hit the security service will be forwarded to real services associated with the security service.
Why we require X-Forwarded-For option:
The X-Forwarded-For (XFF) header is a de-facto standard header for identifying the originating IP address of a client connecting to a web server through an HTTP proxy or a load balancer. When traffic is intercepted between clients and servers, server access logs contain the IP address of the proxy or load balancer only. To see the original IP address of the client, the X-Forwarded-For request header is used.
Please follow below instructions to enable X-Forwarded-For option through webui:
- Login into ASF webui.
- Expand “Application Defense” option under security Defense.
- Click on “HTTP Profile” and click on “Request Security” option.
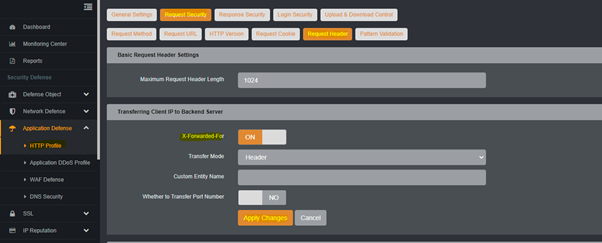
- Click on “Request Header” under “Request Security” options
- Enable the “X-Forwarded-For” option in section “Transferring Client IP to Backend Server”
- Selection value as “Header” in Transfer Mode.
- Click on Apply Changes and save configuration globally.
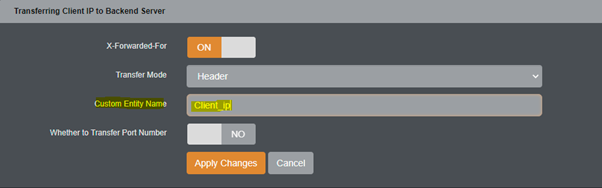
- We can also define custom header name by mentioning the require header name in “Custom Entity Name” option.
Please follow below instructions to enable X-Forwarded-For option through CLI:
- Login into ASF CLI
- Switch to enable mode with command “enable” and enter into confirm mode with command “conf terminal”
- Execute the below command to enable the x-forwarded-for option
#http profile insert request xforwardedfor on "Http_profile_Name" header "X-Forwarded-For"
Note: Please mention the exact http profile name on highlighted section on above command.
Example for enabling the xforwardedfor :
#http profile insert request xforwardedfor on "CLP" header "X-Forwarded-For"
Example for enabling the xforwardedfor with custom header name:
#http profile insert request xforwardedfor on "CLP" header "Client_ip"
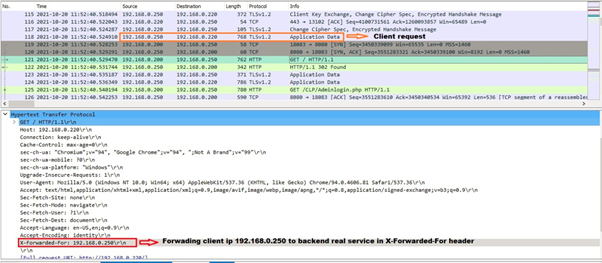
How to verify that ASF is forwarding the client ip to Backend server :
To confirm this, we need to take the debug trace log from ASF. If you are using HTTPS real service then you need to decrypt the debug trace for backend real service communication.
In debug trace, click on http request from ASF to real service and check for header name "X-Forwarded-For". The http request should have the header "X-Forwarded-For" with client ip.