Problem
This solution helps to decrypt packet captures that contains ECDHE cipher based SSL Sessions
Solution
It is not possible to use Private Key to decrypt packet capture when SSL handshake is done using Elliptical Ciphers like ECDHE.
In such scenarios we can make use of SSL Session keys that APV saves when we take packet capture on APV.
Example:
We have a ssl vhost with all ECDHE ciphers
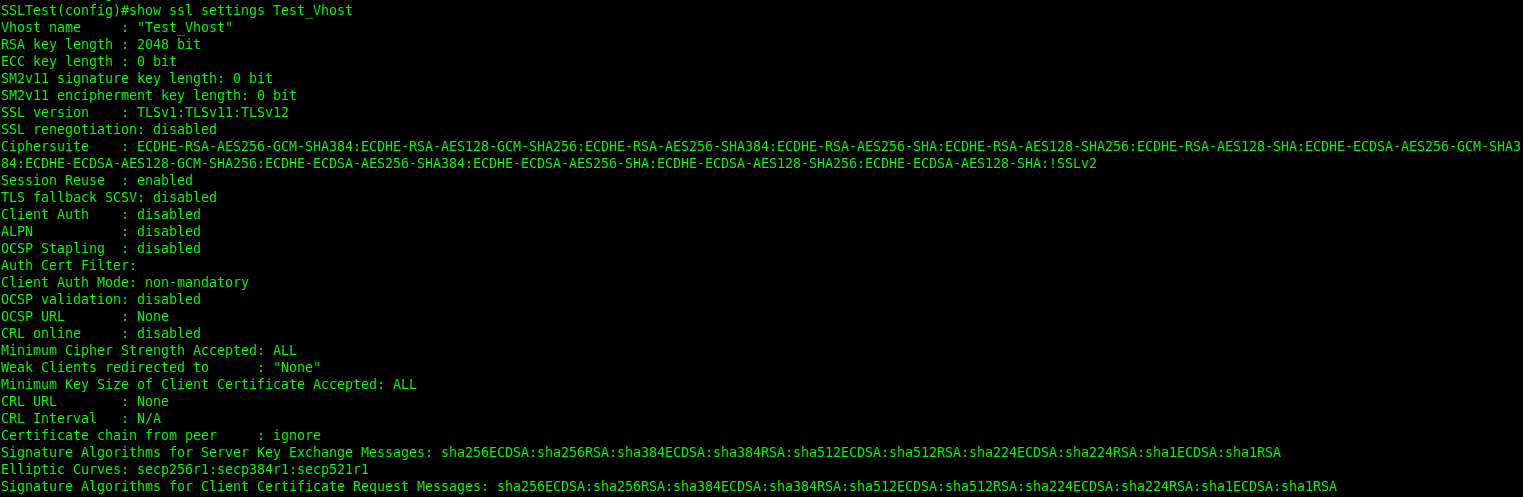
When we access this VIP, we can see cipher negotiated is ECDHE based
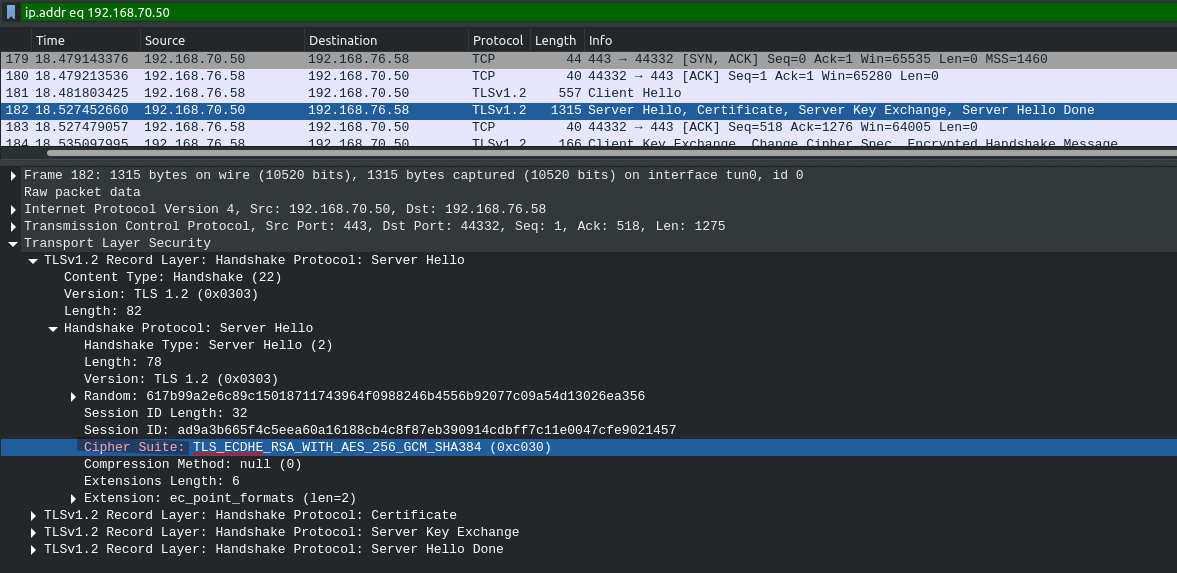
Below packet capture was taken while accessing VIP
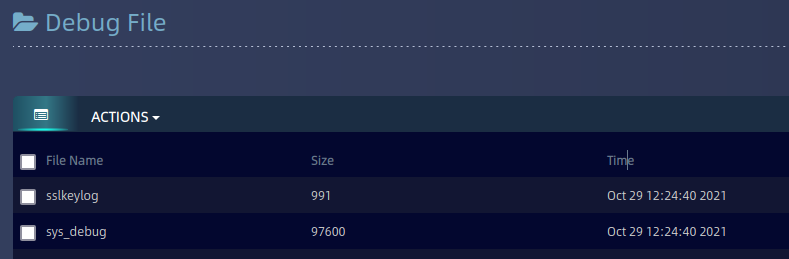
Sslkeylog file is gpg encrypted and hence we need to share sslkeylog file with Array Tech Support to get file decrypted.
After decryption we get a Tar file of sslkeylog

Extract the file to get SSL session keys

Now use this key file in Wireshark to decrypt the SSL traffic.
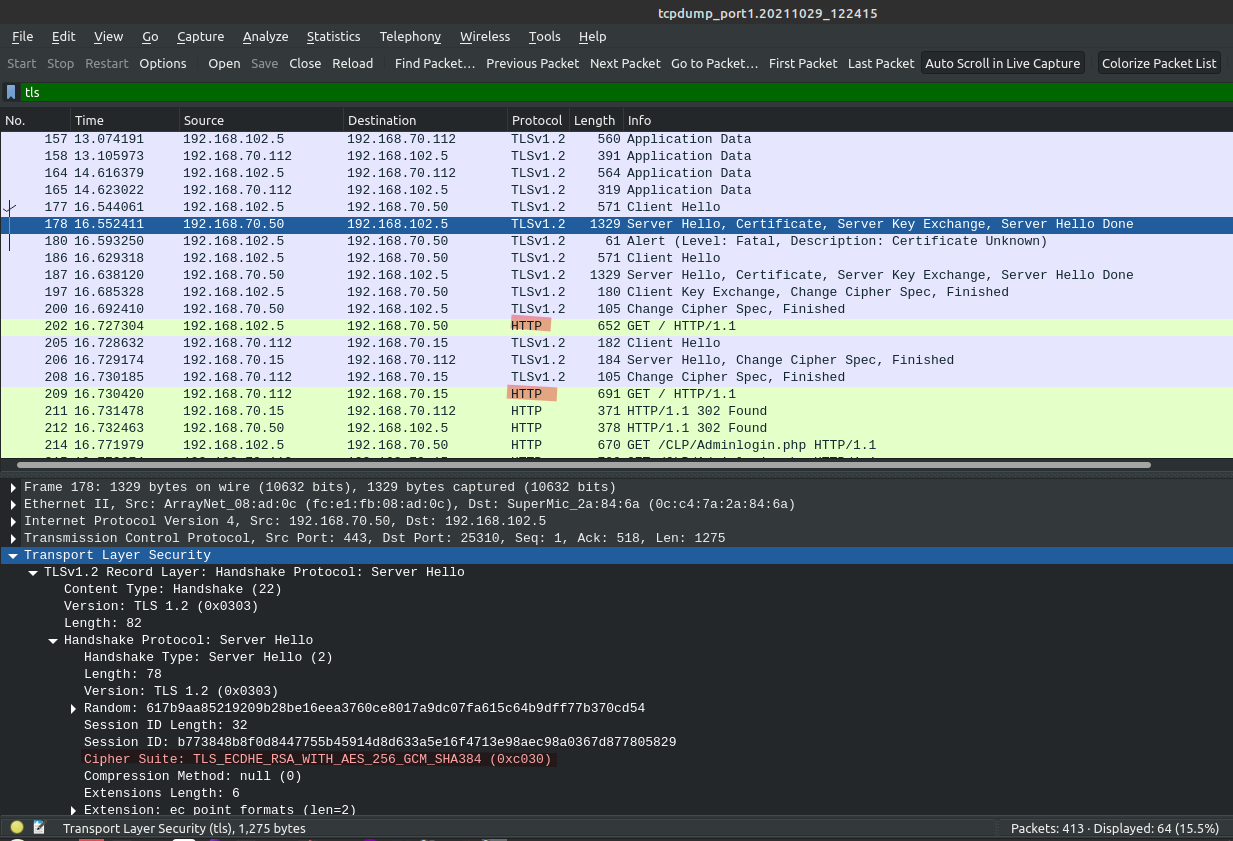
Before decrypting packet capture if we filter for TLS we can see encrypted traffic.
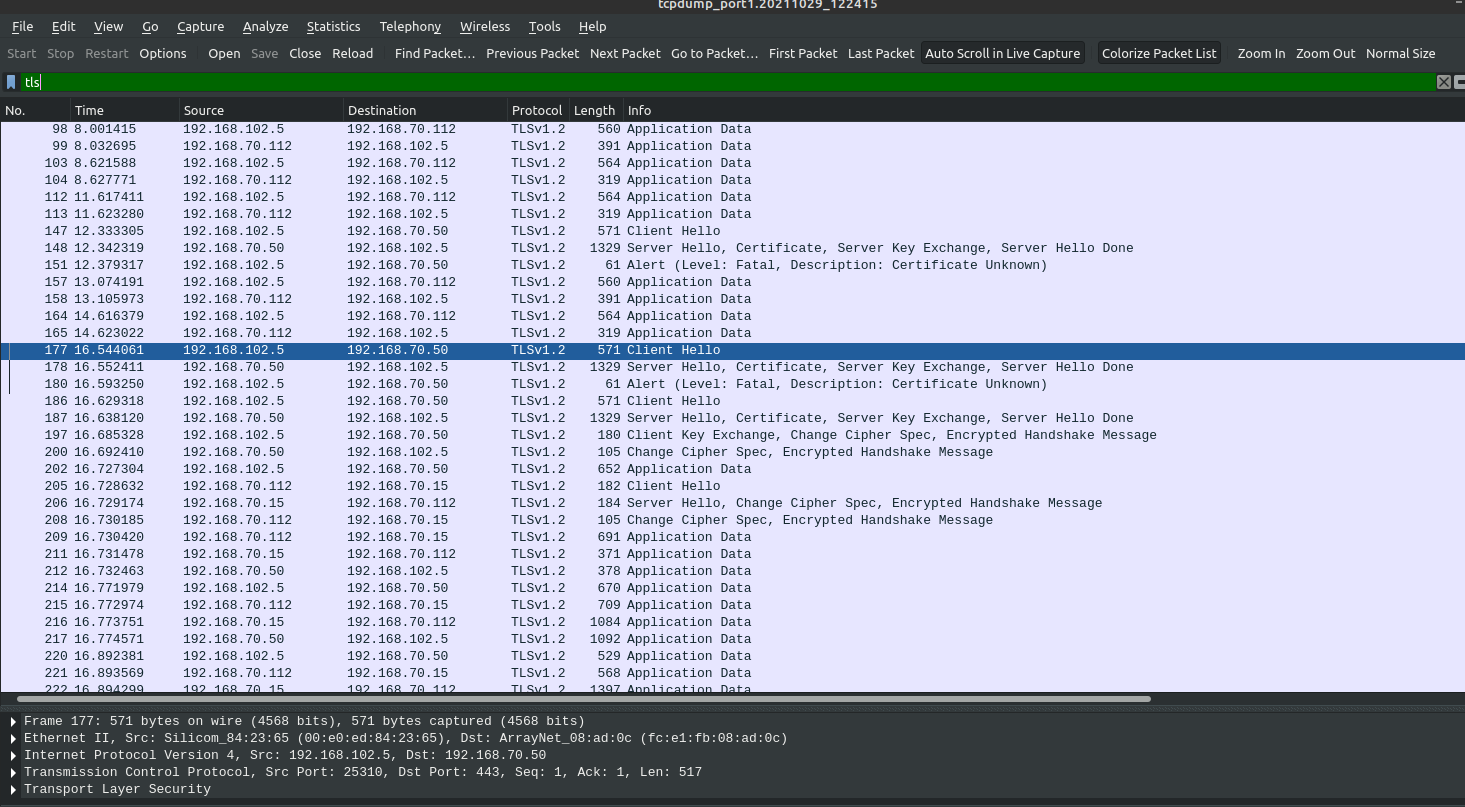
To decrypt follow below steps in Wireshark GUI:
Go to Edit > Preferences >Protocols > TLS > (Pre)-Master-Secret log filename --- Browse and Select the sslkeylog file here [highlighted in RED color]
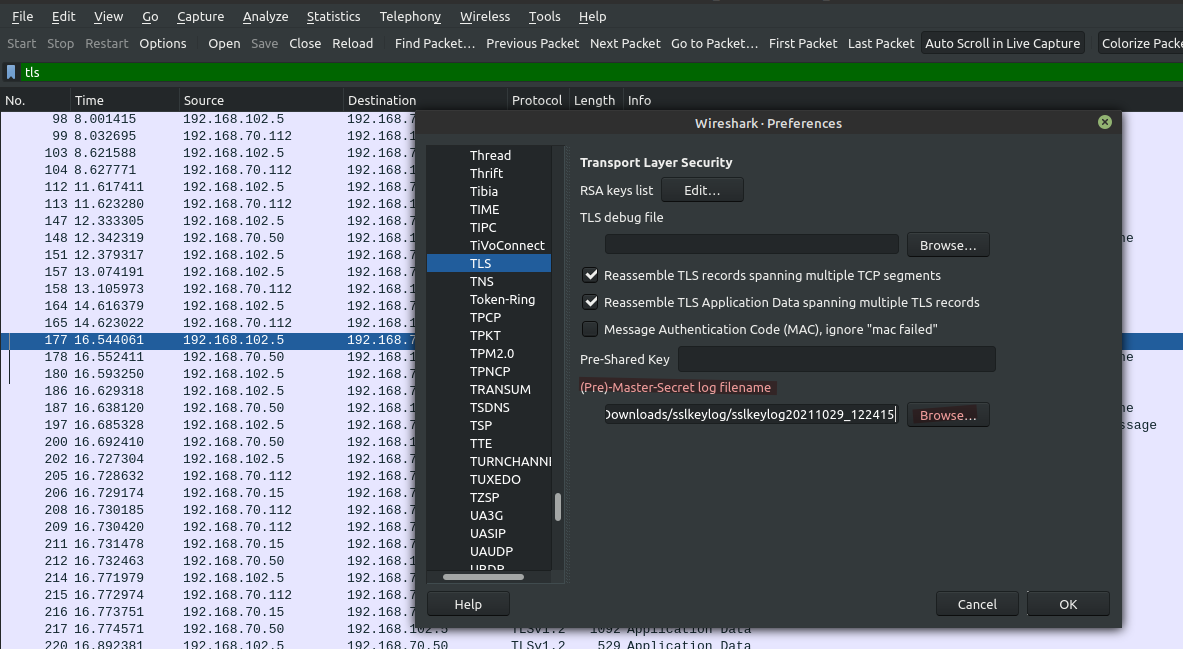
Now you can see that file is decrypted even though cipher negotiated was ECDHE